AWS Security using Identity Access Manager Users and Groups

So if you have never read any of my articles, my name is Steve (although I have recently been dubbed “Peg man” by our Delivery Director’s daughter 😂). I work for a company called Dootrix. The main base is down in Southampton, but we have a cosy team of four up in Manchester 😎.
IAM Users
What is an IAM User?
So IAM stands for Identity Access Management. Even when you have just signed up, you are using it. That is because that is where your root user resides.
With IAM you can create new users and attach specific policies so they can access the resources they need to fulfil their job role. By default a user has no permissions. That means that if you create a new user and don’t attach any policies to them they can’t do anything. They will just see Access Denied when they visit each AWS service.
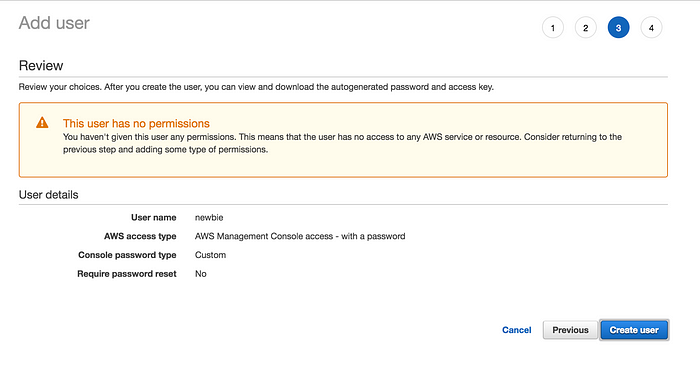
Having no permission by default is rather powerful. It allows you to follow the principal of least privilege. It is easier to have a relaxed security policy where you only add what you need, than to have to create a tightened one where you have to manually deny access to services. Chances are…you’ll miss one 😣.
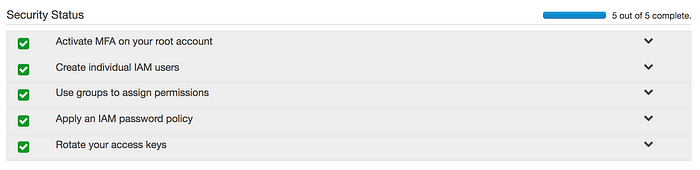
An AWS security check-list
When you first log on to the AWS platform, you will see a check-list on the IAM dashboard. This is so you can follow a standard practice for securing your account. It is advised that you ensure all steps are complete.
Example: Allowing access to a single S3 bucket
In this example we have two S3 buckets. A user will be able to access only one of them, and only be able to download from that bucket.
So we have the buckets:
- final-friday-reports
- final-friday-classified
We want to create a user that can only download what is in final-friday-reports.
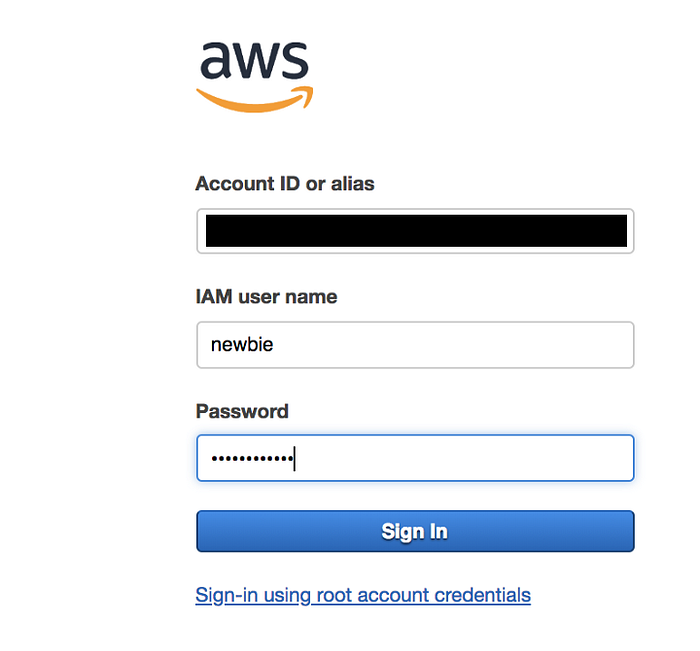
So the first step is to create a user that has no permissions, like newbie 👆
Next we need to create a policy.
Then we need to specify what resources that policy can access. So we will say they can list everything in our final-friday-reports bucket with the ListBucket action, and also download using the GetObject action.
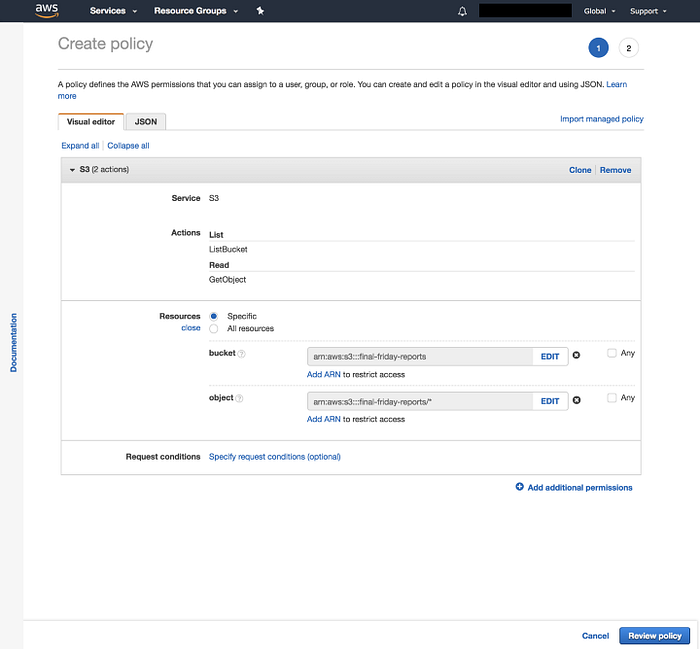
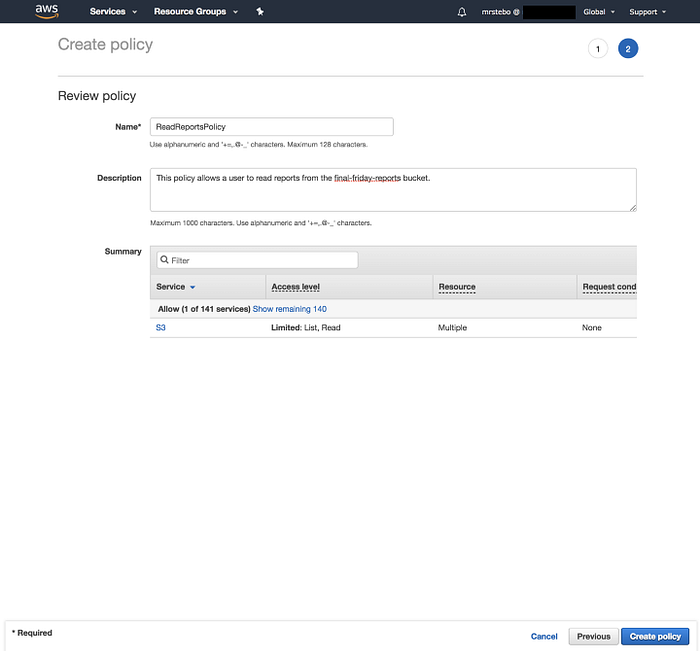
Next we get to the “Review policy” screen where we can give our policy a name and a description. When things look good click “Create policy”.
Testing the policy
So we now have to log in to our new IAM user account.
And then go to the S3 service.
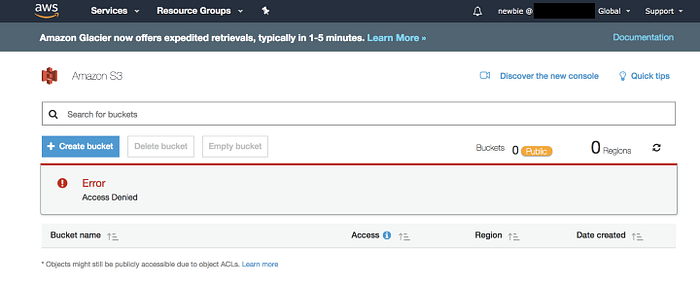
Hmmm…seems like we may have missed something…
Let’s have a look at our policy again 🔍
Seems like we missed an action
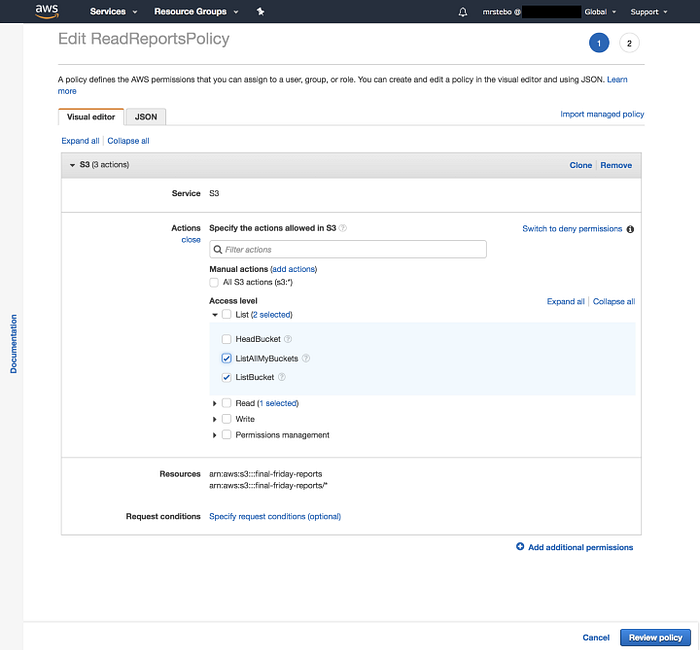
Ah, we need to add the ListAllMyBuckets action! Let’s save this change and go back to S3.
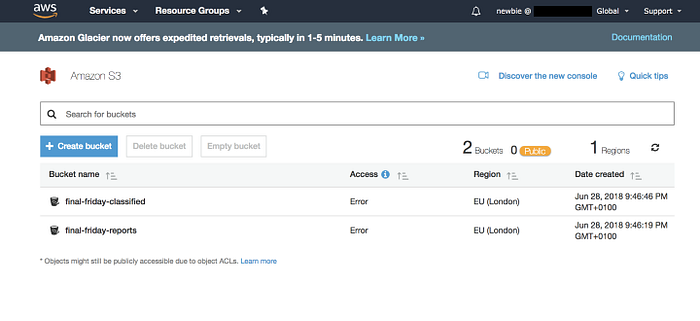
Okay, so we can see all of our buckets.
What happens when we try go inside final-friday-classified?
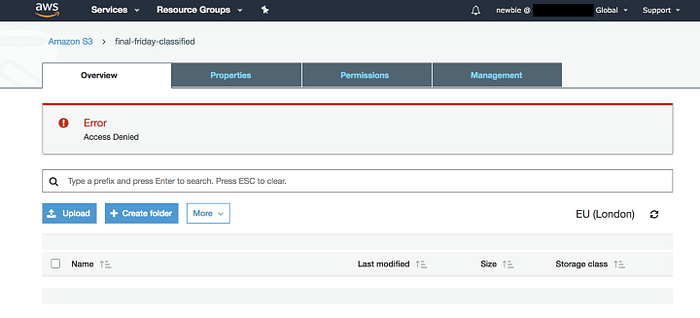
That looks superb. It is just the behaviour we were after. They won’t be able to see any of our classified documents 😎
But let’s check to see if we can see what is in final-friday-reports, because we need to be able to download them.
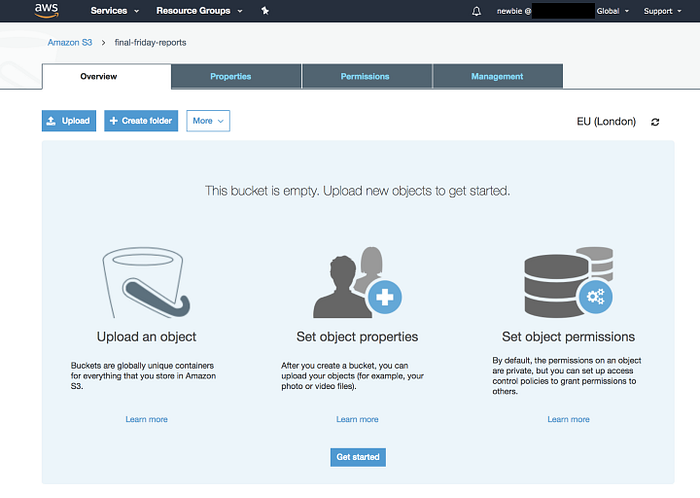
Now, even though there is nothing in there we don’t get the Access Denied banner. So we can safely assume that everything is alright.
In our policy we only allow the GetObject action. So let’s test that we can’t upload a file…
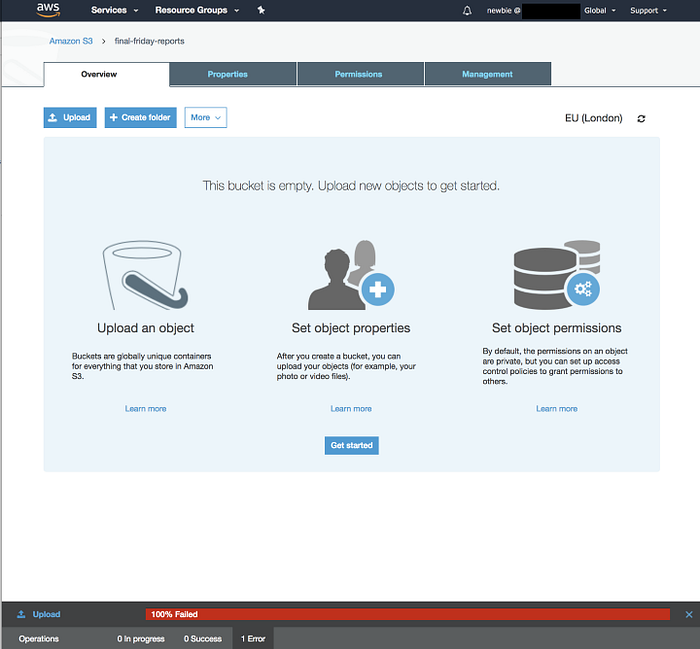
As you can see from the banner at the bottom of the screen, uploading failed! 🎉
And let’s check that we can also download…
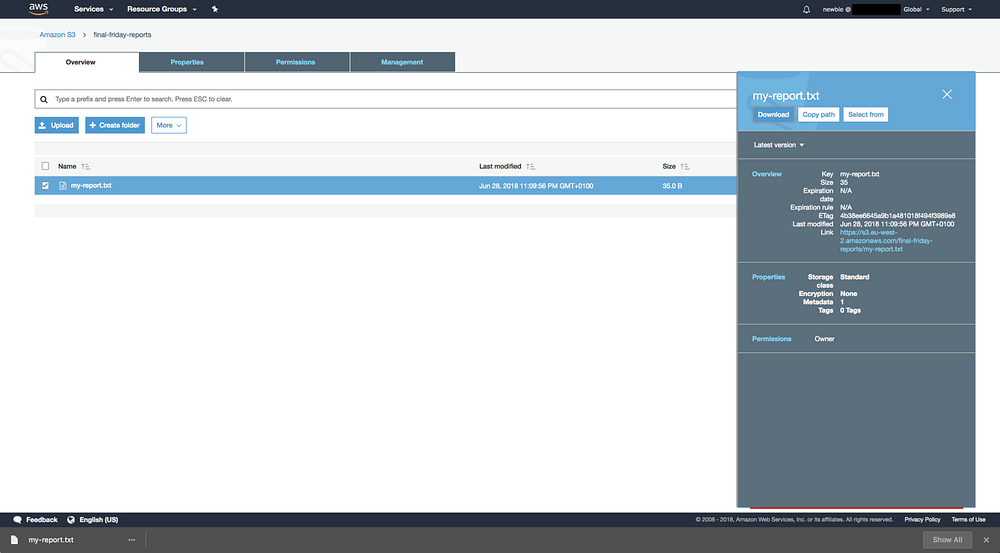
Excellent, it works 👍
IAM Groups
How can I allow multiple users to have the same permissions?
IAM groups allow you to set up policies that affect all users in that group. So you could set up a HR group that can access specific S3 buckets, or a DevOps group that can create resources for multiple services.
By default you have an Administrators service which has access to every AWS service. So be careful when adding users to that group.
Wrapping up
IAM is a simple but powerful service. But with power comes great responsibility 🤓
Users are in essence a container for policies.
Groups are a container for Users that can share common policies.
Don’t use wildcards where possible. Always follow the Least Privilege rule! Only give users access to what they “need” to get the job done.
